Check Point experts have discovered an unusual FreakOut malware that attacks Linux systems and targets unprotected applications running on top of these systems.
Launched in November 2020, the botnet actively crawls the network looking for TerraMaster devices, web applications based on the Zend PHP Framework, and sites running the CMS Liferay Portal.
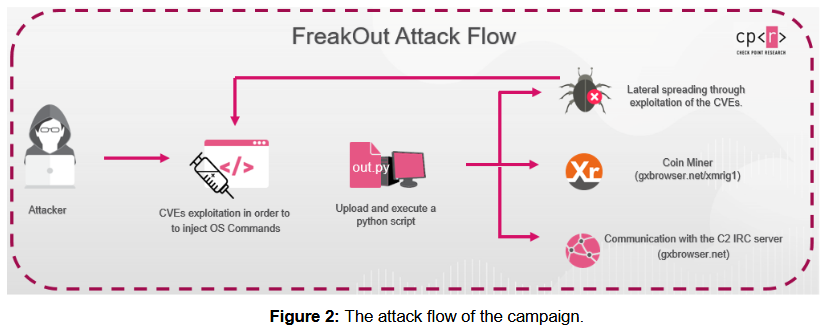
Once targeted applications are discovered, FreakOut operators use exploits against them for three relatively new vulnerabilities, and thus gain control over the underlying Linux system. Since all of the bugs listed below were discovered relatively recently, many users have not yet installed patches, and cybercriminals’ attacks are often successful.
- CVE-2020-28188 — RCE in TerraMaster control panel (bug disclosed on December 24, 2020);
- CVE-2021-3007 — deserialization issue in Zend Framework (bug disclosed on January 3, 2021);
- CVE-2020-7961 — Liferay Portal deserialization issue (bug disclosed on March 20, 2020).
If the attack succeeds, FreakOut immediately downloads and runs a Python script on the infected system that connects infected devices to an IRC channel through which attackers can send commands to bots and launch attacks. So, the list of commands includes:
- collecting information about the infected system;
- creating and sending UDP and TCP packets;
- performing brute-force attacks via Telnet using a prepared list of logins and passwords;
- launching port scanning;
- ARP poisoning in the local network;
- opening a reverse shell on an infected host;
- elimination of local processes.
The researchers write that malware functions can be combined to perform various operations, including launching DDoS attacks, installing miners, turning infected systems into proxies, or organizing attacks on the local network of an infected device.
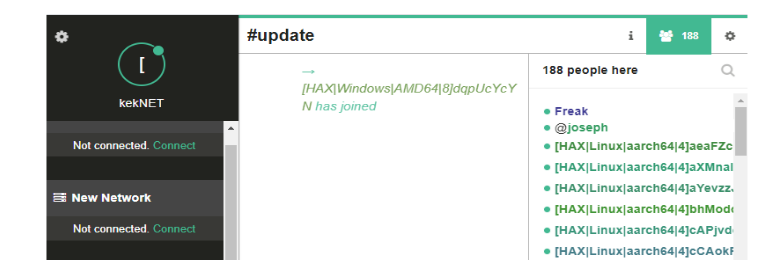
According to experts, the botnet is still young and developing. The company’s analysts managed to reverse the malware and gain access to the hackers’ IRC channel, and the statistics collected in this way indicate that the botnet currently controls only 188 infected systems, while at the peak of their activity there were about 300.
In the FreakOut code it was also possible to identify a number of features, thanks to which the researchers discovered the author of the botnet, a person known under the nickname Freak. According to Check Point, this person is directly related to a certain Fl0urite – the creator of the now inactive N3Cr0m0rPh botnet, which was previously sold on hacker forums and was intended to attack Windows devices.
According to the old advertisements, many of the functionality of the old botnet was identical to FreakOut.
Let me remind you that I talked about the Linux version of Stantinko malware that is now disguised as Apache web server.









