In November of this year, Juniper Threat Labs specialists discovered the Gitpaste-12 malware, which was distributed through GitHub, and also used Pastebin to host malicious code. The number “12” in the name of the malware meant that it was exploiting twelve different vulnerabilities at once.
Eleven of them are listed below, and another is related to Telnet brute-force that Gitpaste-12 uses.
- CVE-2017-14135 Webadmin plugin for opendreambox
- CVE-2020-24217 HiSilicon IPTV/H.264/H.265 video codecs
- CVE-2017-5638 Apache Struts
- CVE-2020-10987 Tenda Routers
- CVE-2014-8361 Miniigd SOAP Service in Realtek SDK
- CVE-2020-15893 UPnP on D-Link routers
- CVE-2013-5948 Asus routers
- EDB-ID: 48225 Netlink GPON routers
- EDB-ID: 40500 AVTECH IP Cameras
- CVE-2019-10758 MongoDB
After the system is compromised, the malware downloads a recursive script from Pastebin and forces the infected host to execute it every minute. Thus, the malware is updated and contacts the C&C server, the address of which is taken from Pastebin. Then the malware downloads the main sell script from GitHub.
Researchers wrote that some commands and hostnames suggested that Gitpaste-12 is intended to attack the cloud computing infrastructure provided by Alibaba Cloud and Tencent. In addition, the malware is equipped with a Monero (XMR) cryptocurrency miner.
However, the malware has the potential of a worm, as it spreads by targeting a list of randomly generated IP addresses within the subnet range.
“Gitpaste-12 contains a script that launches attacks on other machines in an attempt to replicate and spread. It chooses a random/8 CIDR to attack and checks all addresses in this range”, — the report says.
Now Juniper Threat Labs experts have found a new version of Gitpaste-12, which already uses more than 30 exploits (24 of them are unique) for Linux systems, IoT devices and various open source components. For example, the researchers observed a new hacker repository on GitHub containing only three files:
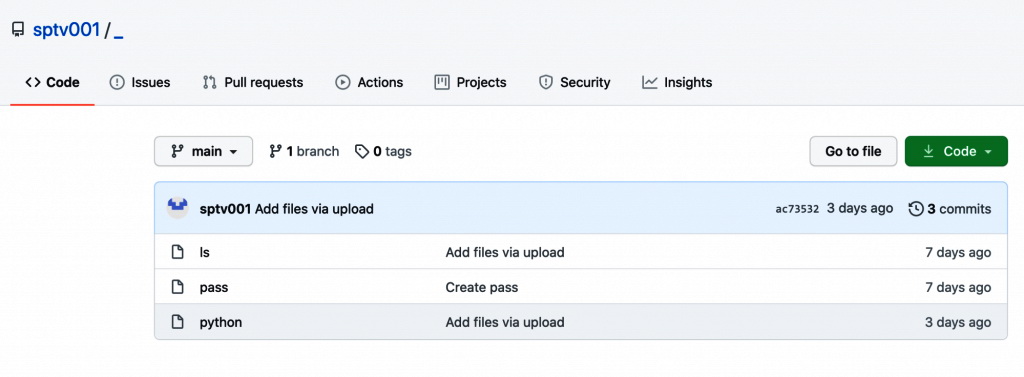
“The attacks used payloads from another GitHub repository, which contained a Linux miner (ls), a list of brute-force passwords (pass) and a statically linked Python 3.9 interpreter of unknown origin”, — the analysts say.
Then two more files were added to the repository: a configuration file (config.json) for the Monero cryptocurrency miner and an exploit for privilege escalation in UPX. As a result, the Gitpaste-12 attack scheme looks like this.
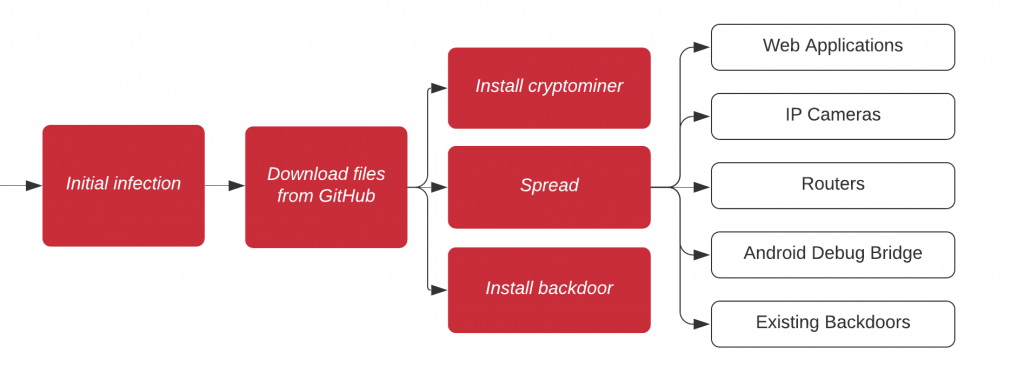
At least seven of the vulnerabilities that exploits the malware were also seen in the previous version of Gitpaste-12, and the malware actively tries to compromise open Android Debug Bridge connections and use backdoors of other malware.
Botnet exploits target JBoss Seam 2, CutePHP, mongo-express, Pi-hole, FuelCMS, and well-known proprietary web applications, including vBulletin.
Let me remind you about the fact that Juniper experts have identified numerous malicious campaigns that use paste sites (instead of conventional C&C servers) to deliver payloads.









