Trustwave’s specialists have discovered an unusual campaign to distribute the NanoCore Trojan – the malware disguises itself as fake Zipx files.
In emails, spammers use fake .zipx files, which are actually icons with additional information in .rar format. All of this is intended to make it harder to detect malware and help bypass filters.
Attackers’ emails, as a rule, are written on behalf of the “purchasing manager” of some organization (most often, the mail of the target’s business partner is forged).
These phishing emails contain an attachment named “NEW PURCHASE ORDER.pdf *.zipx”, but the file does not meet the .zipx specification. In fact, it is a “surprise icon file,” as the experts put it. That is, it is an image binary with additional information attached in the .rar format – a malicious EXE file that contains a payload.
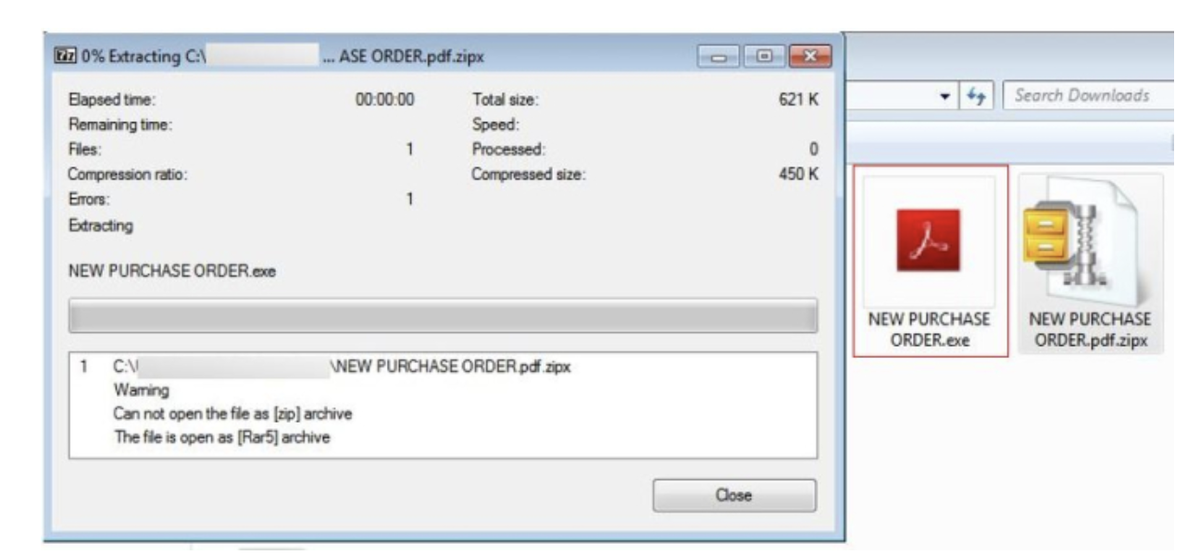
If the victim falls for the scammers’ bait and clicks on the attachment, and an archiver (WinZip or WinRAR) is installed on his machine, the executable file is extracted. 7Zip can also unpack such a file, but this may require more than one attempt – sometimes the archiver reports an error.
“Analysis of the EXE files shows that they are samples of NanoCore RAT version 1.2.2.0. It creates copies of itself in the AppData folder and injects malicious code into the RegSvcs.exe process”, — the experts write.
In a slight twist, enclosing the executable into a RAR archive instead of a ZIP file, the content of the .zipx attachment can be extracted by another popular archiving tool, 7Zip. If the end-user uses 7Zip or WinRAR, the NanoCore malware could be installed onto the system, if the user decides to run and extract it. It all works because various archive utilities try their darndest to find something to unzip within files.
Let me remind you that NanoCore was first discovered back in 2013. Having penetrated the system, it collects email addresses and passwords, and also activates the webcams of infected devices. Malware can act as a dropper for additional malware, as well as a platform for creating botnets using infected hosts for DDoS attacks.
It should be noted that the Trojan’s developer, Taylor Huddleston, was convicted in the US back in 2018, however, as you can see, his case still lives on.
Let me remind you that also Spanish law enforcers arrested FluBot malware operators.









