Kaspersky Lab experts have discovered the new Moriya rootkit for Windows, a quite rare type of malware. The fact is that after the release of Windows 10, OS security has noticeably increased, so in recent years it has become much more difficult to develop and successfully use rootkits.
The researchers write that Moriya is designed for Windows and has existed since at least 2018, but until recently the rootkit went unnoticed. According to the company, during this time it was used for very limited and narrowly targeted attacks (so far less than a dozen victims).
The most notable victims were two large regional diplomatic organizations in Southeast Asia and Africa, with the remainder in South Asian countries.
Who exactly is the creator of this rootkit is unknown, but researchers believe that some Chinese cyber espionage group is behind the malware.
“We rely on the fact that victims have previously been attacked by Chinese-speaking hackers and are usually located in countries that are often targeted by such criminals. In addition, the tools used by the attackers, including China Chopper, BOUNCER, Termite and Earthworm, are additional indicators to support our hypothesis, as they were previously used in campaigns attributed to well-known Chinese groups”, — the report says.
Moriya went unnoticed for so many years, because, for example, it uses a well-known tactic: it is embedded between the Windows TCP/IP network stack and incoming network traffic, and then intercepts data packets before they even reach the operating system and any locally installed antivirus.
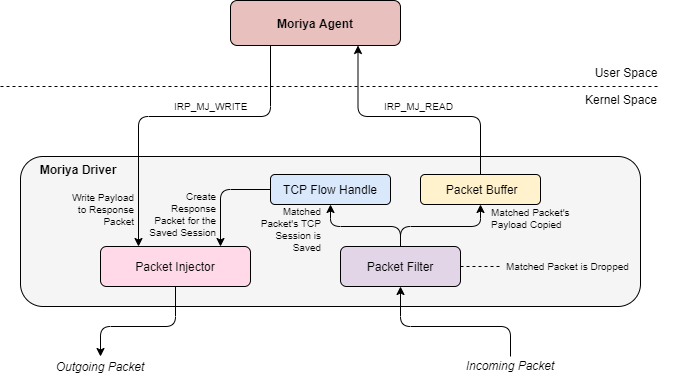
To infiltrate the network of an organization of interest and install Moriya, attackers typically compromised vulnerable IIS web servers. For example, in one of the confirmed attacks, the entry point was a server that did not have a patch for the old CVE-2017-7269 vulnerability. Exploiting this bug, the attackers installed a web shell on the server and then used it to deploy Moriya.
Let me remind you that I also wrote that Malware Purple Fox was updated and received a self-propagation mechanism.









