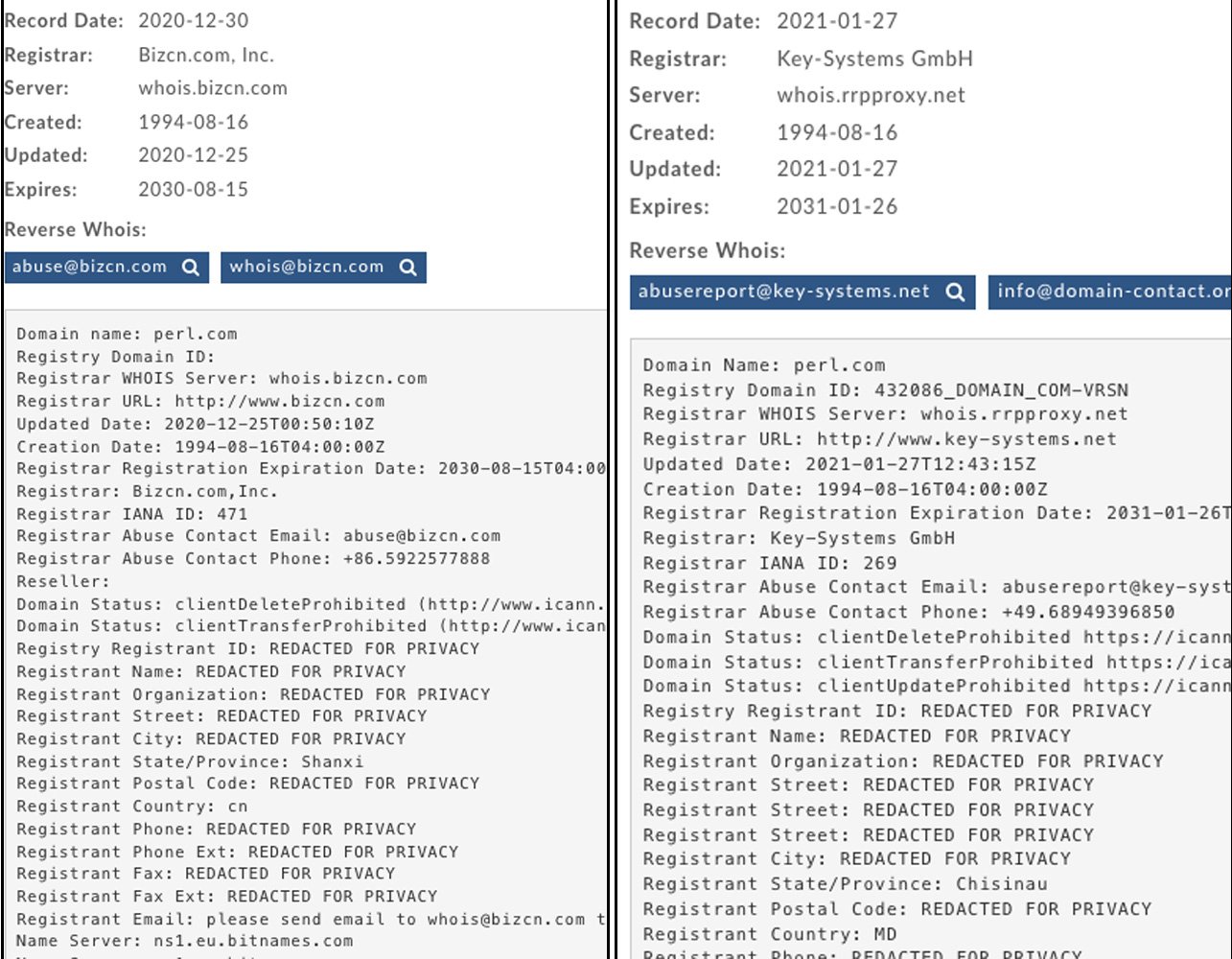
Unknown attackers occupied the perl.com domain, owned by Tom Christiansen, who has been using it since 1997 to post news and articles about the Perl language.
The first problem with the site noticed its editor Brian Di Foy last week, who wrote on Twitter that the domain was unexpectedly registered by an unknown person.Soon, IP attorney John Berryhill responded to the post, reporting that the domain was stolen back in September 2020, when it was associated with the registrar Network Solutions.
Then, during the Christmas holidays, the domain was transferred to a registrar in China and finally, on January 27, 2021, it was transferred to the Key-Systems registrar. Only then the IP address assigned to the domain was changed from 151.101.2.132 to the Google Cloud IP address 35.186.238[.]101.
Currently, site visitors see only a blank page, the code of which contains scripts typical of the parked Godaddy domain, although in fact it is registered with key-systems[.]net.
Di Foy writes that so far, the perl[.]com content has been temporarily moved to perldotcom.perl.org. He advises against using perl[.]com as a CPAN mirror for now.
Di Foy also told Bleeping Computer journalists that the domain owner’s account was not hacked, and now the problem the domain is being solved together with Network solutions and Key-Systems specialists:
“I spoke directly with Network solutions and Key-Systems and I know that they are working on this, and so far, the perl.com domain is blocked. Tom Christiansen, its rightful owner, is currently undergoing recovery [access] with these registrars.”
Interestingly, the IP address now associated with perl[.]com has long been used in malicious campaigns. So, in 2019, the IP address 35.186.238[.]101 was tied to the domain distributing the executable file for the now Locky defunct ransomware.
Recently, a malicious clicker-like adware (VirusTotal) was seen using the command servers at www.supernetforme[.]com and www.superwebbysearch[.]com, and both of these domains also resolved to 35.186.238[.]101.
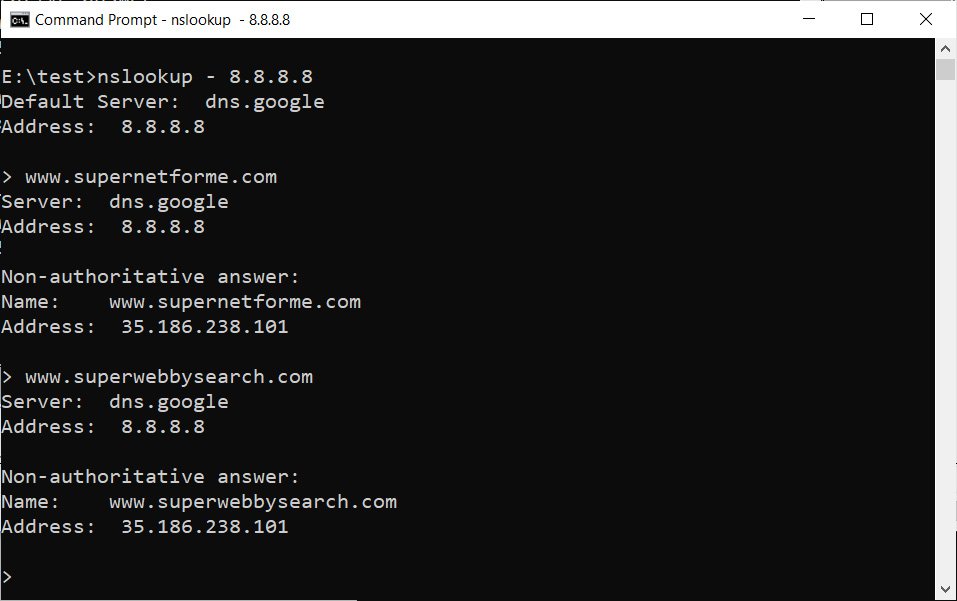
When malware tries to connect to the URLs of those domains, it gets the same parked domain scripts currently used on perl[.]com. While these HTML responses do not resemble the instructions from the command and control server, they may indicate that the IP address is under the control of another attacker.
In short, currently visiting perl[.]com is strongly discouraged until the domain is back under the control of the Perl Foundation.
Let me remind you that the IObit forum was hacked and used for sending DeroHE ransomware to the participants.







