Trend Micro warns that VPNFilter-infected devices can still be found worldwide. Several years ago, this malware infected at least half a million routers and NAS manufactured by Asus, Linksys, MikroTik, Huawei, TP-Link, Ubiquiti, NETGEAR, UPVEL and ZTE in 54 countries.
Even then, experts noted the similarity between VPNFilter and the BlackEnergy malware. It is believed to have been created by a group of allegedly Russian government hackers APT28, also known as Fancy Bear, Pawn Storm, Strontium, Sofacy, Sednit, Tsar Team, X-agent, Sednit, and so on. Due to this fact, representatives of the FBI and the US Department of Justice said that VPNFilter is a development of Russian government hackers.
More than two years later, analysts have tried to determine if a botnet is a threat now. To do this, Trend Micro researchers turned to colleagues from the Shadowserver Foundation, who work with Cisco Talos, the FBI and the US Department of Justice, to sinkhole the toknowall[.]com domain from where VPNFilter obtained the addresses of the command servers.
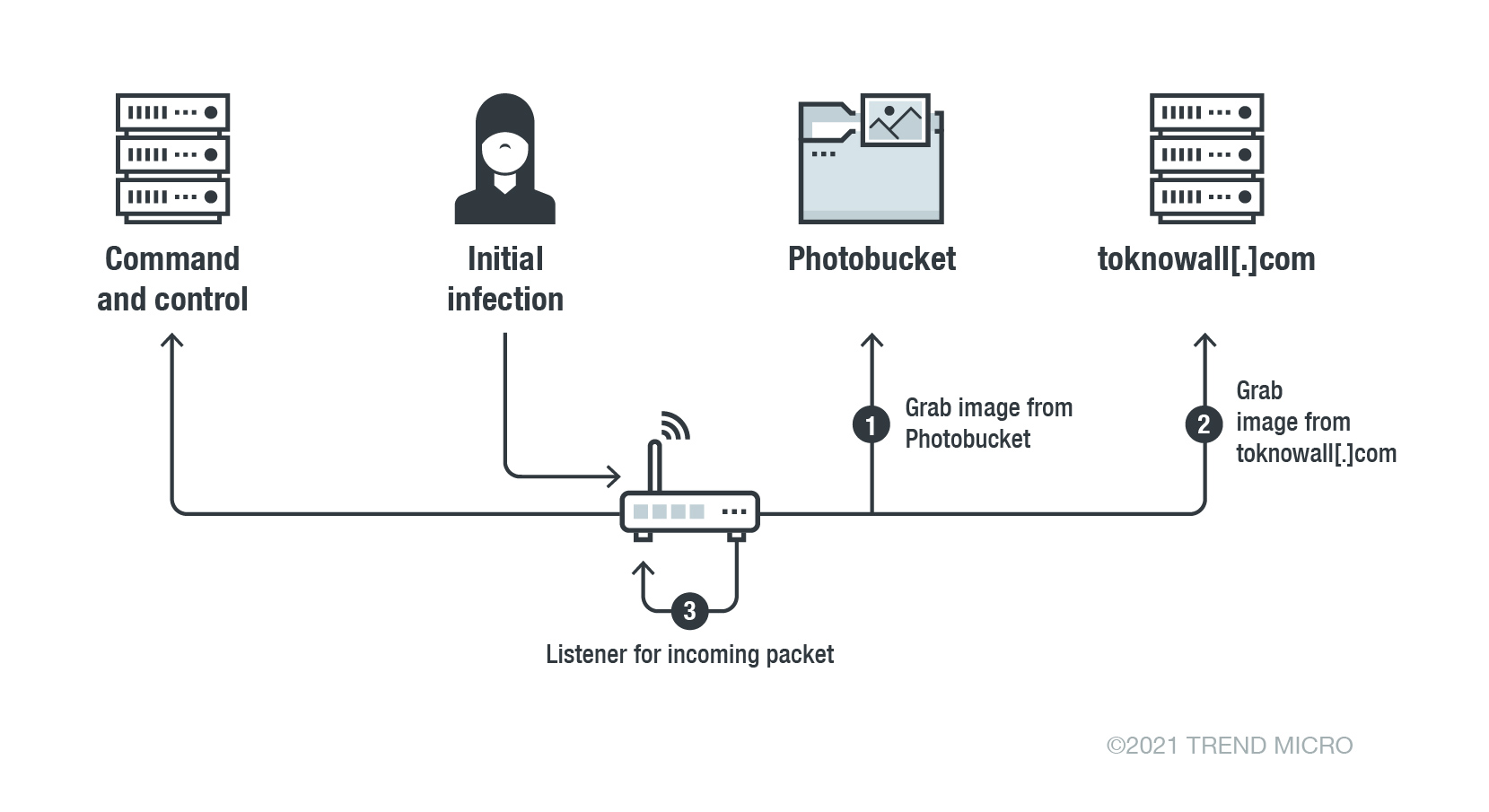
It turned out that 5447 unique devices regularly access the domain, that is, they are still infected. At the same time, the real number of infections should be even higher, since this domain can be blocked by many companies at the DNS level.

Researchers also tested whether it was possible to transfer a new IP address to infected devices in order to understand how many of them were waiting for second-level payloads. For doing this was created and sent a special packet that made possible to determine that the 1801 networks responded to it, while another 363 networks tried to contact the sinkhole server through TCP port 443.
“Although only 363 networks have connected to our sinkhole, we cannot say that the 1801 networks that initially responded positively are clean. They can also be infected with VPNFilter, but the connection to our sinkhole could be blocked if they were behind a firewall”, — write the experts.
Trend Micro warns that these networks can be easily hijacked by any attacker who understands how VPNFilter works. What is worse, the hackers who created the malware and stand behind the original malware campaign can also try to regain control of infected devices at any time.
Let me remind you that I also talked about PyMICROPSIA malware for Windows that can also be used for attacks on Linux and macOS.









