Researchers from Morphisec talked about the Jupyter malware that steals data from browsers. Jupiter is written in .NET and found on the network of an unnamed US educational institution.
According to experts, the Trojan has been active since at least May of this year and is primarily aimed at stealing data from the Chromium, Firefox and Chrome browsers.
“Jupyter is an infostealer that primarily targets Chromium, Firefox, and Chrome browser data. However, its attack chain, delivery, and loader demonstrate additional capabilities for full backdoor functionality”, — wrote Morphisec researchers.
As mentioned above, the malware also tries to create a persistent backdoor on the compromised system that allows attackers to execute PowerShell scripts and commands, and also allows attackers to download and execute additional malware.
The Jupyter installer is usually an executable file hidden in a ZIP archive. This executable file is often masked using Microsoft Word icons and filenames that prompt the user to open them immediately (supposedly related to important travel or pay raises).
Once installed on a system, Jupyter steals data from the victim’s browser, including usernames, passwords, autocomplete data, browsing history, and cookies. The malware sends the collected information to its command and control server.
“Jupyter developer is constantly modifying and supplementing the original Jupyter in an effort to collect as much information as possible about the compromised machines. It is not yet clear what the ultimate goal of this campaign is, but in theory, stolen data can be used for sale, and hackers can use compromised machines as entry points into companies’ networks for further attacks”, — write the researchers.
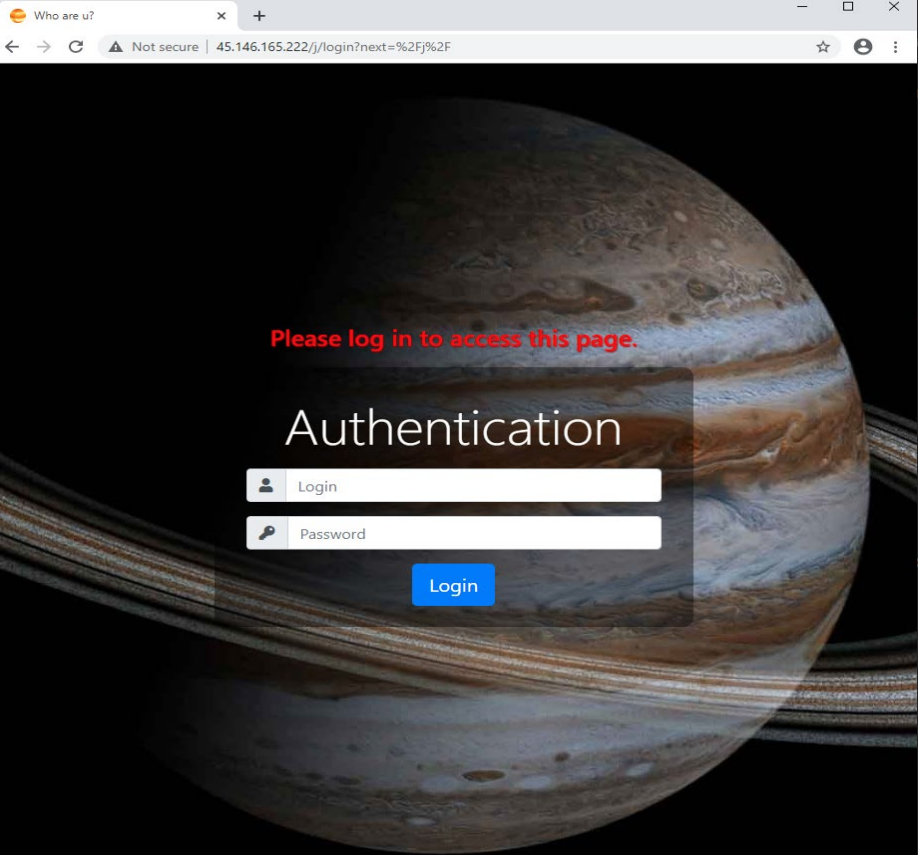
According to Morphisec experts, Jupyter was developed in Russia. For example, the control servers of the malware are located on the territory of the Russian Federation, and in the administrative panel of the malware can be found an image of the planet Jupiter, the original image of which was found on a Russian-language hacker forum.
Moreover, the picture is signed exactly as “Jupyter”, although the name of the planet is translated into English as “Jupiter”, that is, the author of the malware does not seem to know English very well.
Let me also remind that the US Cyber Command uploaded to VirusTotal new versions of the ComRAT and Zebrocy malware, the authorship of which are attributed to Russian government hackers. Also power engineering company Schneider Electric has warned its customers about the Drovorub malware developed by Russian hackers.









