While investigating the recent attack on SolarWinds and its customers, CrowdStrike experts said they had discovered the third malware involved in this operation. The malware was named Sunspot.
According to Microsoft’s report, in the attack were involved two malwares: Supernova and CosmicGale.
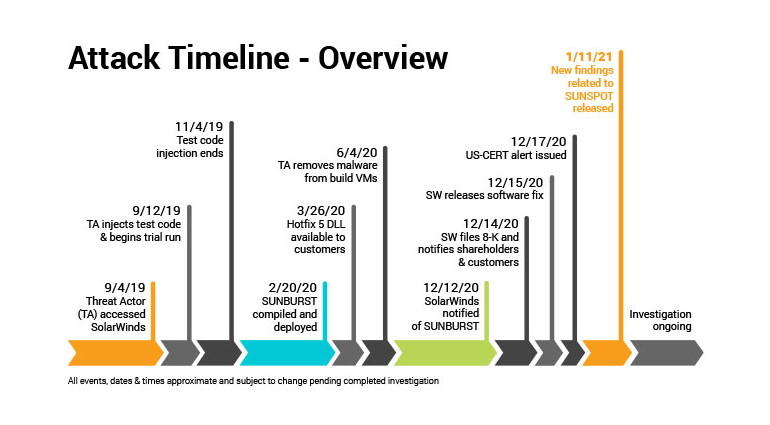
The Crowdstrike report states that although Sunspot malware was the last detected, hackers used it first: it was deployed back in September 2019, when attackers first entered SolarWinds’ internal network. Then Sunspot was installed on the company’s build server.
This malware had one single purpose – it had to monitor the build server while waiting for commands related to the Orion platform, which was eventually compromised by the cybercriminals, and the company’s clients installed infected versions. So, if Sunspot found a build command for Orion, it subtly replaced files inside the application with malicious files with the SUNBURST backdoor.
“SUNSPOT is StellarParticle’s malware used to insert the SUNBURST backdoor into software builds of the SolarWinds Orion IT management product. SUNSPOT monitors running processes for those involved in compilation of the Orion product and replaces one of the source files to include the SUNBURST backdoor code. Several safeguards were added to SUNSPOT to avoid the Orion builds from failing, potentially alerting developers to the adversary’s presence”, — say CrowdStrike experts.
When the infected version of Orion was installed on the networks of clients (companies and government agencies), SUNBURST wasactivated, collecting data on victims, and then sending this information to its operators. If, in the end, the hackers decided that the victim was a promising target for the attack, they removed SUNBURST and replaced it with the more powerful Teardrop backdoor Trojan.
Analysis of the SolarWinds software build server revealed how exactly StellarParticle intercepted this process to insert SUNSPOT into service packs.
“The SUNSPOT design assumes that the StellarParticle developers applied considerable afforts to ensure that the code is inserted correctly and stays unnoticed, so SolarWinds developers can hide their presence in the build environment”, – told in CrowdStrike.
Let me remind you the US government announces new versions of ComRAT and Zebrocy malware.







