Recently, I saw a plenty of messages like “my internet browser demonstrates to me unwanted Heders-gadfly.xyz pop-up advertisements, is it a pc virus?” or “these Heders-gadfly.xyz pop-up advertisements in my Chrome making me insane, how to take care of them?”. According to the statistics for last months, pc virus distributors began a vast adware circulation project. Let me demonstrate you, how you can get rid of the viruses from your personal computer, and forget about the frustrating Heders-gadfly.xyz pop-ups.





Pop-Ups : Discovering The Nature
You can admit that some sites (like a Heders-gadfly.xyz) show you pop-up ads. The message can have something like “do you want to have notices about the current information?” or “allow notifications to be reported regarding new discount rates?”. Usually, such messages are safe, and may only sidetrack you with its abrupt arrival. Moreover, it can be quite easily disabled, in case notifications from this web page are no longer needed.
Pop-up notifications are quite an effective advertising instrument. If you have an interest in products of some kind, you can allow pop-ups from the internet site where you can acquire this stuff, and as soon as these products are in inventory again, or if you can have a discount – you will certainly obtain the notice concerning this. The counterparty – online sellers, automobile lending companies, etc – will certainly be in profit, too – customer will certainly obtain a tip regarding the item he/she intended to pay for. And also such an advertising and marketing method is almost free – this element is really crucial for companies.
| Site | Heders-gadfly.xyz |
| IP Address | 188.40.110.143 |
| Infection Type | Adware, Push notifications, Unwanted Ads, Pop-up Ads |
| Symptoms | Annoying pop-up ads in the right corner. |
| Similar behavior | Playgamego.xyz, News-kakego.cc, News-gafivi.cc |
Heders-gadfly.xyz Pop-Ups Are Not So Safe
But sometimes pop-up ads can come out without your approval, as well as with an information which is totally various from your current attentions or search queries. And also, besides undesirable Heders-gadfly.xyz pop-ups from the unknown origin, you can simultaneously see a lot of advertisements, including ones on the web pages which at first have no ads whatsoever. Such a scenario can be the signal of adware existence.
Adware is the kind of malware which infiltrates into your computer, after that begins demonstrating to you different promotions. Their content usually has no connection with your regular search queries. Besides banner ads, your web browser can also demonstrate you a big quantity of various Heders-gadfly.xyz pop-up promotions, which come into view in the bottom right area.
The model of adware usage is very sly. The big pack of adware is spread through trojan viruses, which are injected in your desktop previously. Promotions, which are demonstrated to you by virus, are paid by their creators. In a couple of weeks, all antivirus programs began to block these adware, thus, trojan loses in profitability. And to ruin the user’s computer, malware distributors begin ransomware distribution with these trojans.
Even if there is no active ransomware distribution, your computer system may continue to be affected by adware virus. A big amount of ads along with Heders-gadfly.xyz pop-ups can make your PC as slow-moving as snail, so your typical jobs will be difficult to perform in common way.
How Can I Deal With Heders-gadfly.xyz Pop-Ups?
Thinking the text above: your PC, and your data, is in a severe danger. To stop this infection, you require to make use of security tool. Microsoft Defender, which is installed in every Windows 10 distribution, has the ability to take care of Heders-gadfly.xyz pop-ups virus. Nevertheless, it can’t change the browser alterations which were applied by malicious program. Another downside of the anti-virus by Microsoft is its particular susceptability: viruses can disable Microsoft Defender with the Group Policies after being implanted to your computer system.
To be 100% sure that your computer is clean of any malware now, and will be clean in future, I can offer you to use GridinSoft Anti-Malware.
To detect and eliminate all unwanted programs on your PC, including Heders-gadfly.xyz pop-ups virus, with GridinSoft Anti-Malware, it’s better to utilize Standard or Full scan. Quick Scan is not able to find all the malicious apps, because it scans only the most popular registry entries and directories.
You can see the detected malicious apps sorted by their possible hazard during the scan process. But to perform any actions against malware, you need to wait until the scan is finished, or to stop the scan.
![]()
To set the action for every detected virus or unwanted program, click the arrow in front of the name of detected malware. By default, all malware will be removed to quarantine.

Reset browser settings to original ones
To reset your browser settings, you are required to use the Reset Browser Settings option. This action is not able to be intercepted by Heders-gadfly.xyz malware, hence, you will surely see the result. This option can be located in the Tools tab.

After choosing the Reset Browser Settings option, the menu will be displayed, where you can specify, which settings will be reverted to original.

Reset browser setiings without making use of third-party software
Besides using anti-malware programs for browser reset, you may pick the “Reset browser settings” function, which is usually embedded in all popular browsers.
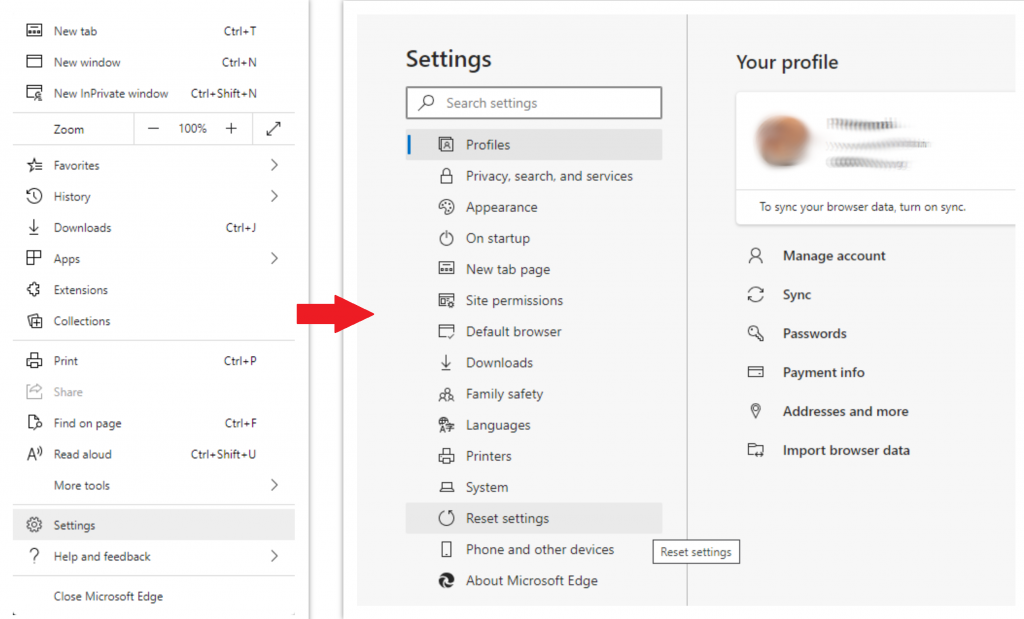
Reset Microsoft Edge  Settings
Settings
- Open "Settings and more" tab in upper right corner, then find here "Settings" button. In the appeared menu, choose "Reset settings" option:
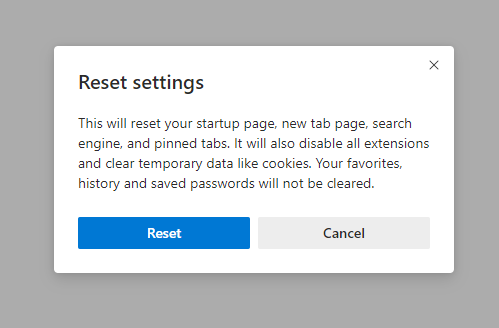
- After picking the Reset Settings option, you will see the following menu, stating about the settings which will be reverted to original:
Reset Mozilla Firefox  Settings
Settings
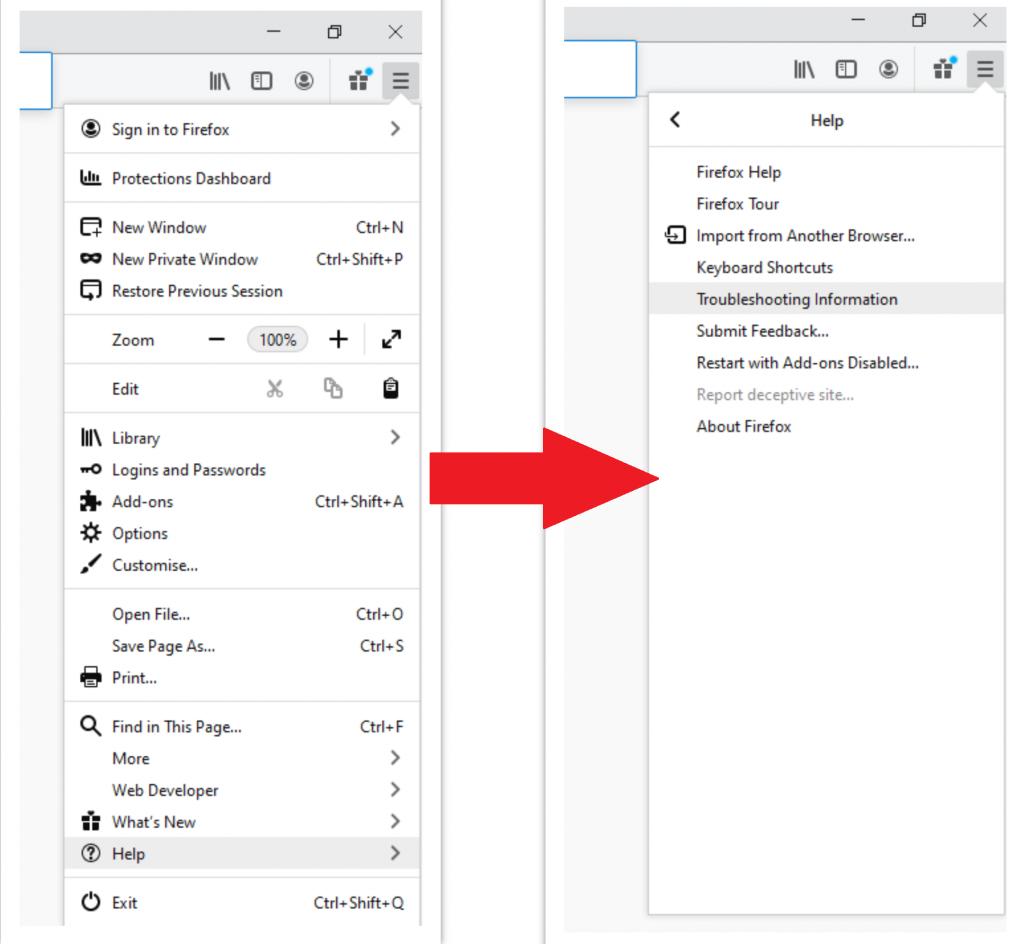
- Open Menu tab (three strips in upper right corner) and click the "Help" button. In the appeared menu choose "troubleshooting information":
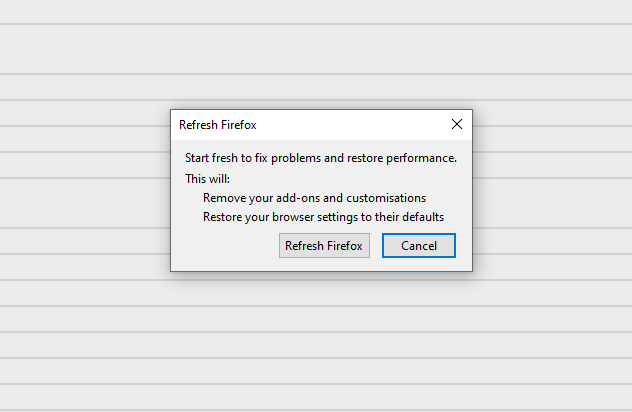
- In the next screen, find the "Refresh Firefox" option:
- Open Settings menu by pressing the gear icon in the toolbar (left side of the browser window), then click "Advanced" option, and choose "Browser" button in the drop-down list. Scroll down, to the bottom of the settings menu. Find there "Restore settings to their original defaults" option:
- After clicking the "Restore settings..." button, you will see the window, where all settings, which will be reset, are shown:
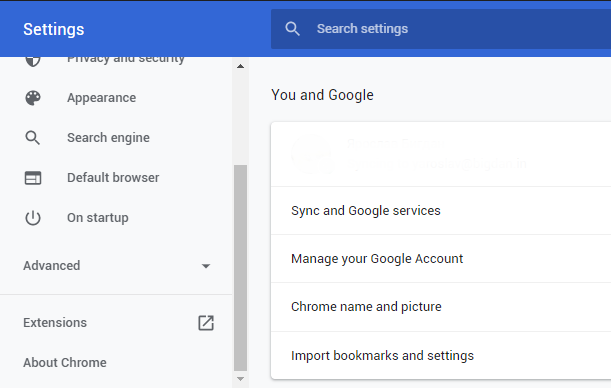
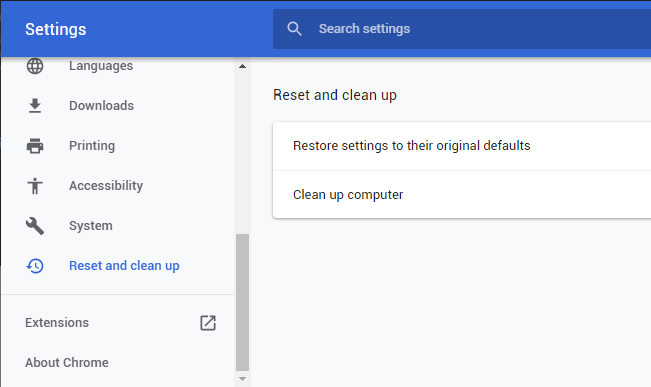
- Open Settings tab, find the "Advanced" button. In the extended tab choose the "Reset and clean up" button:
- In the appeared list, click on the "Restore settings to their original defaults":
- Finally, you will see the window, where you can see all the settings which will be reset to default:
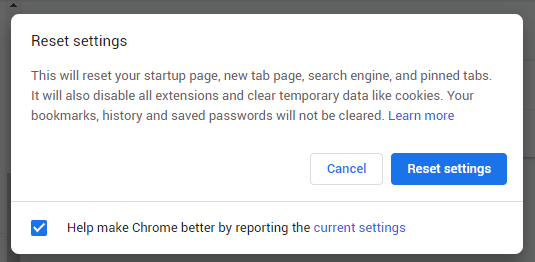
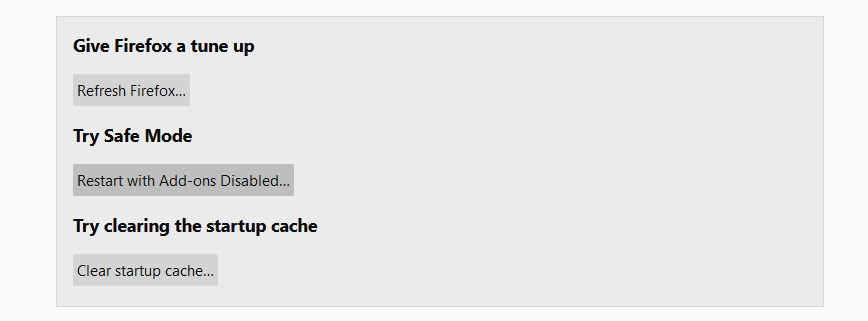 After choosing this option, you will see the next message:
After choosing this option, you will see the next message:
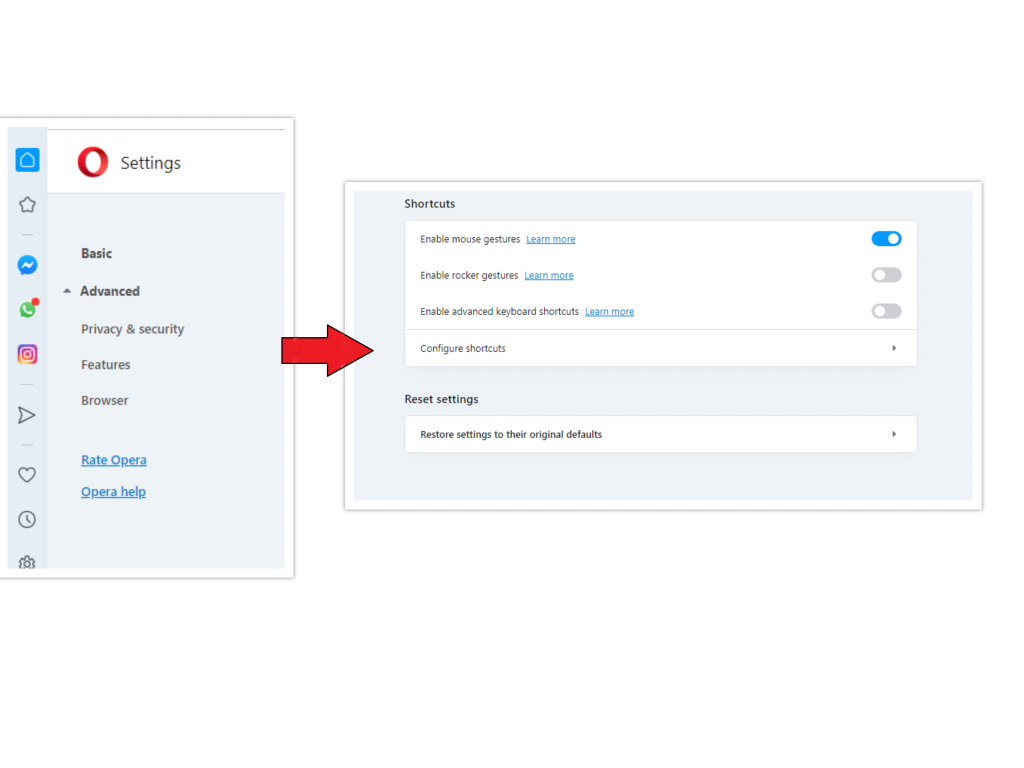
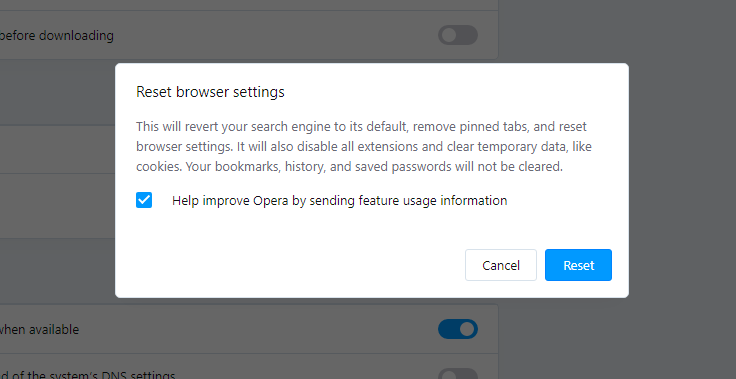
Reset Opera  Settings
Settings
Reset Google Chrome  Settings
Settings
As an afterword, I want to say that the time plays against you and your PC. The activity of browser hijacker Heders-gadfly.xyz must be stopped as soon as possible, because of possibility of other malware injection. This malware can be downloaded autonomously, or offered for you to download in one of the windows with advertisements, which are shown to you by the hijacker. You need to act as fast as you can.









