Cisco Talos specialists have discovered a new variant of the Masslogger Trojan, which now mainly attacks users from Turkey, Latvia and Italy, expanding the geography of its activity. The fact is, at the end of 2020, the malware targeted users in Spain, Bulgaria, Lithuania, Hungary, Estonia and Romania, but it looks like the malware’s targets are now changing almost monthly.
Masslogger is designed to steal credentials and is also a keylogger (this functionality appears to be disabled in this version of the Trojan). It is capable of stealing data via SMTP, FTP or HTTP. And while the first two options do not require additional server components, theft via HTTP is carried out through a web application in the malware control panel.
The malware currently steals logged in data from Discord, Microsoft Outlook, Mozilla Thunderbird, NordVPN, FileZilla, Pidgin, FoxMail, Firefox, QQ Browser and Chromium-based browsers (Chrome, Chromium, Edge, Opera, Brave).
Masslogger was first spotted by experts back in April 2020, but has now changed significantly. The newest Masslogger is distributed via phishing emails and is enclosed in a multivolume RAR archive. The malware uses the .chm format and the .r00 extensions, which especially interested experts.
“CHM is a compiled HTML file that contains an embedded HTML file with JavaScript code to start the infection process. Each stage of infection is heavily obfuscated to avoid detection using simple signatures”, — the experts say, mentioning that this file format is commonly used in Windows Help.
If you open a malicious attachment and .chm, a fake help window will appear and a payload will be triggered
This ultimately leads to the deployment of a PowerShell script that contains the Masslogger loader itself. The loader is usually located on compromised legitimate hosts, and the file name usually contains one letter and one number with the extension .jpg. For example, “D9.jpg”.
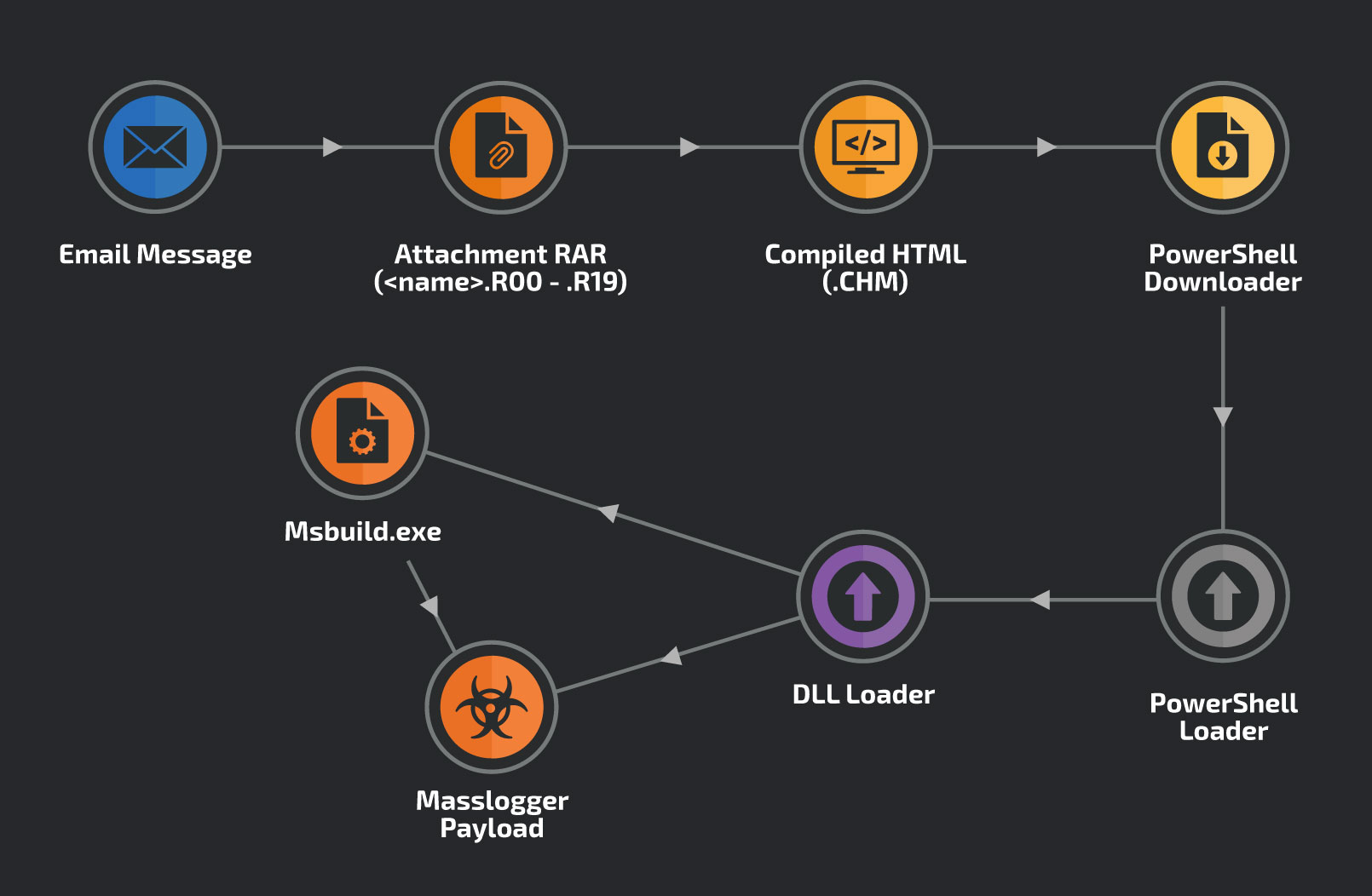
At the same time, experts emphasize that the malware is almost completely executed and is present only in memory. The only component on disk is the mail attachment and the compiled HTML file.
Let me remind you that I also reported that Popular Chrome Extension The Great Suspender Contained Malware.









