
Specialists of the Chinese company Qihoo 360 have discovered a new malware, or rather the Matryosh DDoS botnet, which attacks Android devices accessible on the Internet via ADB (Android Debug Bridge).
Although ADB is disabled by default on most Android devices, some gadgets are shipped with enabled ADB (most commonly on port 5555). As a result, ADB has long been a known source of problems for smartphones, TVs, set-top boxes and other “smart” devices running Android.For example, earlier the debugging functions of the OS were abused by malware such as Ares, Trinity, Fbot, and ADB.Miner.
“360 netlab BotMon system labeled a suspicious ELF file as Mirai, but the network traffic did not match Mirai’s characteristics. This anomaly caught our attention, and after analysis, we determined that it was a new botnet that reused the Mirai framework, propagated through the ADB interface, and targeted Android-like devices with the main purpose of DDoS attacks”, — Qihoo 360 experts told the story of malware detection.
Now the researchers write that Matryosh differs from other similar botnets as it uses Tor to hide its control servers, and a complex multi-level process is used to obtain the address of this server itself, which gave the botnet its name – by analogy with a Russian doll.
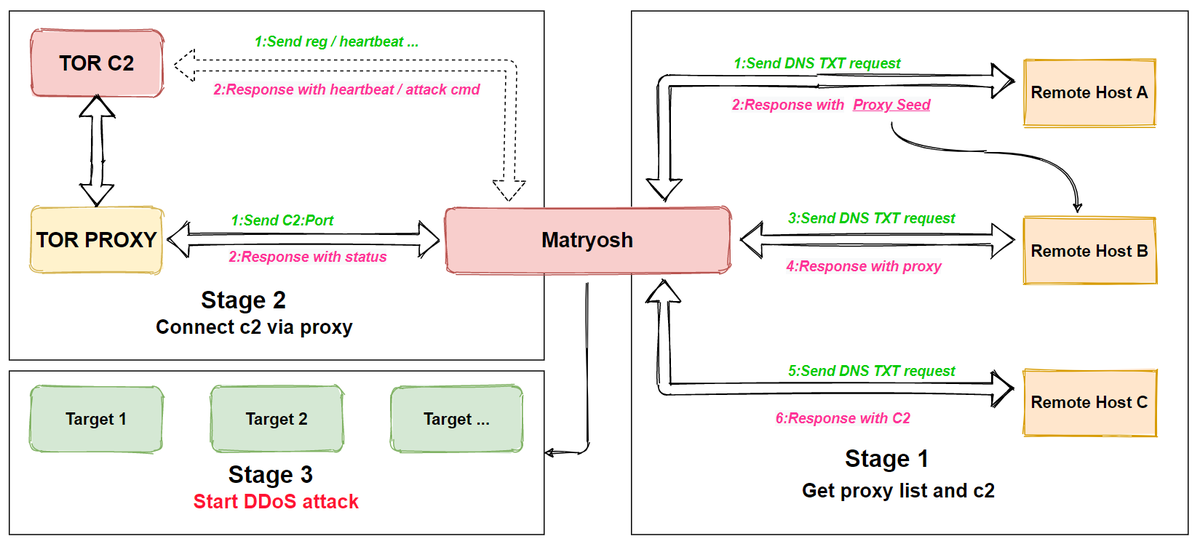
According to Qihoo 360, the same hacker group that created the Moobot botnet in 2019 and the LeetHozer botnet in 2020 may be behind the development of this malware.
Both of these malware were used to organize DDoS attacks, as well as Matryosh, which is capable of launching attacks using TCP, UDP and ICMP.
“Matryosh has no integrated scanning, vulnerability exploitation modules, its the main function are DDoS attack, it supports tcpraw, icmpecho, udpplain attacks and the basic scheme is shown in the following figure”, — Qihoo 360 researchers say.
Also, experts note possible problems in recognizing malware. Matryosh’s cryptographic design is somewhat new, they said, but still refers to Mirai’s single-byte XOR pattern, so anti-virus software easily marks it as Mirai.
Let me remind you that I also wrote that specialists from Check Point have discovered a new Rogue malware for remote access on Android.