The BazarCall (or BazaCall) malware was first discovered in January 2021, and now experts have found out that it is distributed through underground call centres.
The malware got this name due to the fact that at first it was used to spread BazarLoader. And although now BazarCall is distributing another malware, its name remained.
BazarCall operators follow a simple but very effective scheme. It traditionally starts with phishing emails, and in order to attract the attention of a future victim, hackers use decoys associated with free trials of various products and supposedly expiring subscriptions for medical, IT or financial services (which must be canceled urgently in order to avoid being charged).
At the same time, all letters contain instructions, according to which, to cancel the subscription, the recipient must call the specified phone number.
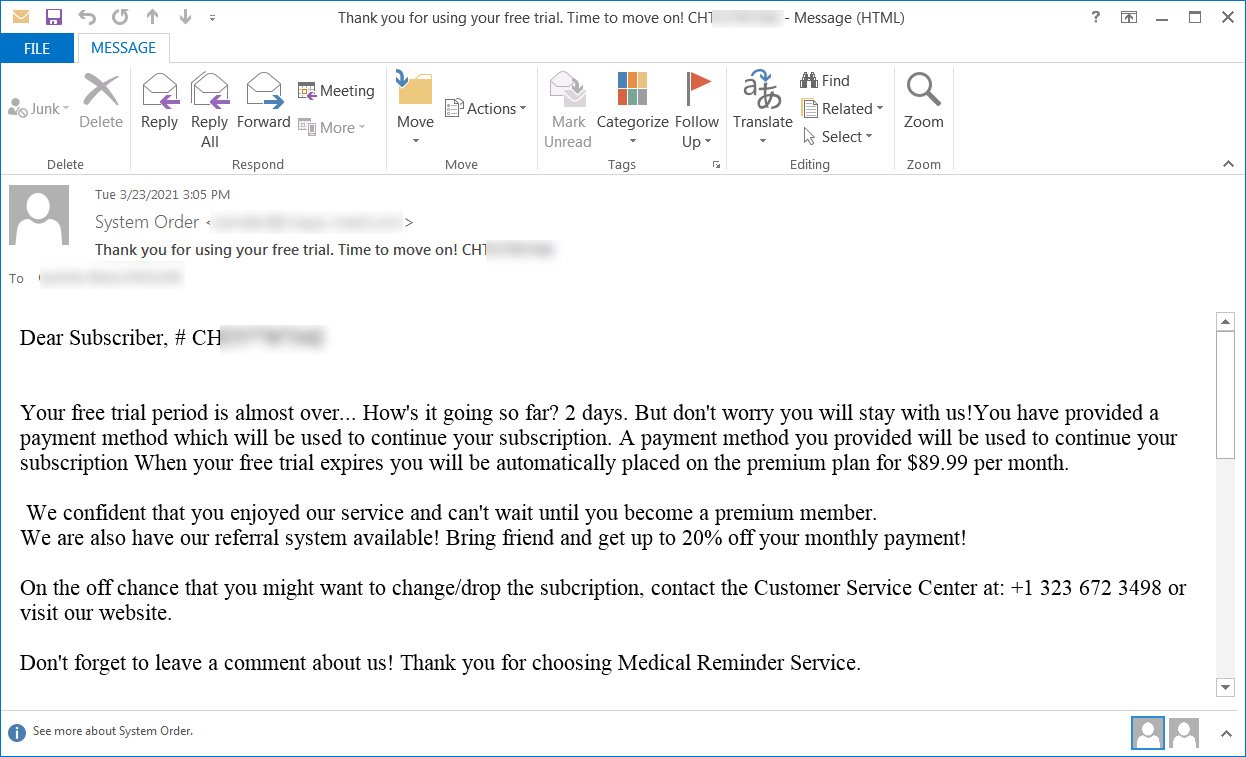
By calling this number, the user contacts the call center, whose English-speaking operator will conduct a step-by-step instruction for the victim.
First, the operator will force the gullible user to provide the unique customer identifier specified in the letter. Thus, the call centre will identify victims of the BazarCall campaign. If you provide an incorrect number, the operator will say that the subscription has already been cancelled and will say goodbye.
If the number is valid, the caller will be forced to visit a malicious site and download an Office file (usually Excel or Word) from there, allegedly containing a form to unsubscribe. Then you need to disable security features and enable macros in the document, which will load the BazarLoader. In some cases, the operator may also ask the victim to disable the antivirus.
One of these calls was recorded and published on YouTube by information security expert Brad Duncan:
These spam campaigns almost always target users with corporate email addresses or addresses in the .edu zone. That is, hackers almost never attack ordinary users who use free email services, including Gmail, Hotmail and Yahoo. Obviously, the ultimate goal of cybercriminals is to infect large corporate networks.
“Due to the exotic method of distribution, the malware has a low detection rate on VirusTotal, because it is not distributed publicly and is poorly detected by antivirus software”, — information security experts say.
Currently, BazarLoader is used to distribute malware such as TrickBot, IcedID, Gozi IFSB, and so on. In turn, Trickbot is used to deploy Ryuk or Conti ransomware, while IcedID was previously used to deploy Maze and Egregor ransomware.
Interestingly, the connection between BazarCall and TrickBot was previously discovered by the well-known cybersecurity expert Vitaly Kremez – it is believed that both malware samples were created by the same hack group. However, BazarCall is not associated with other malware listed above.
Bleeping Computer writes that, according to Binary Defense analysts, the fraudulent call centre is operated by another hack group, for which the distribution of malware is a common service. At the same time, the call centre works like a regular company: from Monday to Friday, following regular business hours.
In recent days, it has not been possible to contact the criminals’ call centre due to the constantly changing infrastructure. Due to the increased interest on the part of IS specialists, criminals are forced to change phone numbers and hosting very often.
Let me remind you that I also talked about the fact that Trustwave’s specialists have discovered an unusual campaign to distribute the NanoCore Trojan – the malware disguises itself as fake Zipx files.









